The recent Equifax data breach affecting 145 million records has been a sensational story. Equifax is one of the three credit agencies (Equifax, Experian and Trans Union) that track our most sensitive personal financial information, so the thought of cyber-thieves getting that information is scary. What, if anything, should you do about it?
The first step is to determine whether or not your personal information has been exposed, because Equifax is just the latest victim in a string of data breaches. Even if you have found that your personal information was not in the Equifax hack (see box), it could have been compromised in another data breach. For perspective, visit the excellent infographic at informationisbeautiful.com. To check if your email address has been compromised, go to haveibeenpwned.com/ and enter your email address. My search there revealed that ALL of my email addresses have been compromised. Based on this, it is not unreasonable to assume that some of your data has been compromised.
What to Do About the Equifax Data Breach
Equifax is offering a free credit monitoring service for a year, which is better than nothing. There is good information from the Federal Trade Commission here:
https://www.consumer.ftc.gov/blog/2017/09/equifax-data-breach-what-do
I recommend following their instructions to find out if your data was breached. I found out that my information was affected, and I signed up for the service.
Completing the Equifax online signup forms will not give Equifax any information that they don’t already have. They ask for your name and the last six digits of your Social Security Number in order to verify your identity. They already have that information, and much more. As long as you are on your home computer, with up-to-date anti-virus software, you should be safe to enter your information on the Equifax website.
The next step is to put identity theft in perspective and decide what to do about it. How much money could an identity thief steal from you? How else can identity theft affect you? How much effort do you want to put into protecting yourself from these consequences? There are two types of identity theft: Account Takeover and Identity Takeover.
- Account Takeover – Using your information to make charges and transfers in your legitimate accounts (usually bank, credit card, or brokerage accounts).
- Identity Takeover – Using your personal information to open new credit accounts, file fraudulent tax returns in order to obtain refunds, receive healthcare services, or apply for other financial benefits.
It is relatively easy to protect yourself from account takeover, but it is much more difficult to protect yourself from identity takeover.Account Takeover
Most account takeover liability is limited by law, as long as you report it on time. The table below lists the potential exposure by type of account. As long as you monitor your accounts regularly (monthly for credit cards, daily for debit cards), your exposure is limited (See table 1).
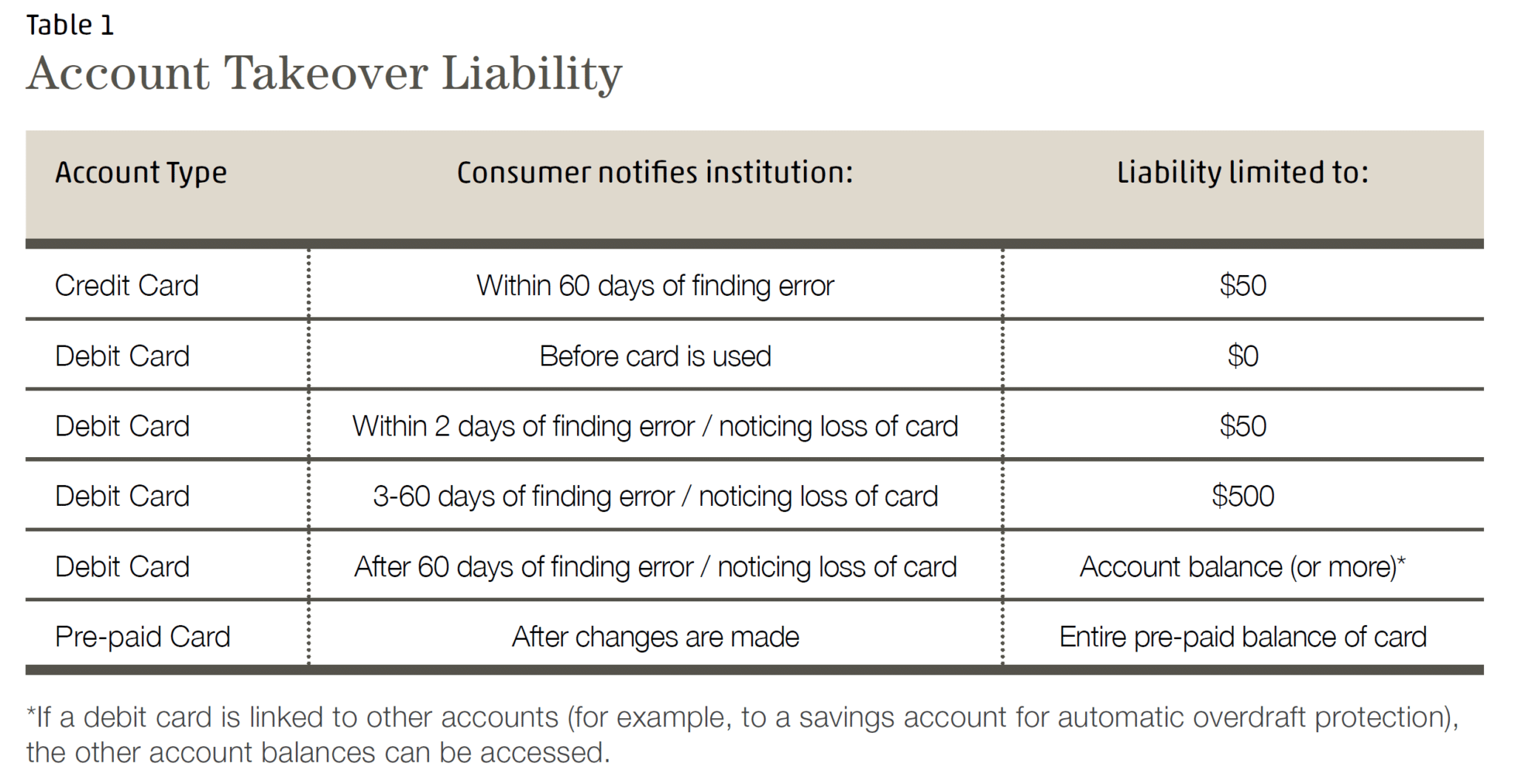
Because these limits exist, it is relatively easy to limit your financial exposure to account takeover. The liability limits to account takeover are time-sensitive, especially for debit cards. The most effective ways to limit your exposure are:- Monitor your debit accounts daily
- Implement alerts on your debit and credit card accounts to catch suspicious transactions early, such as geographic, transaction, or account balance limits
- Review your credit card statements monthly, as soon as possible after you receive them
- Do not link large savings accounts to your debit card account
Identity Takeover
Identity takeover is a less common, but more difficult to resolve, problem. Although the consumer’s responsibility for the fraudulent accounts and charges is normally low, the time and money spent repairing identity takeover can be significant. Protecting against identity takeover involves keeping your own information safe, but also monitoring for signs that your identity may have been stolen from a third party.
To prevent others from obtaining your personal information, I recommend the Security Checklist (recently updated) on our website. Even after taking the measures listed on our checklist, you should also monitor your credit information to identify identity takeover and limit the damage it can cause. Table 2 below lists common steps you can take, along with the pros and cons of each.
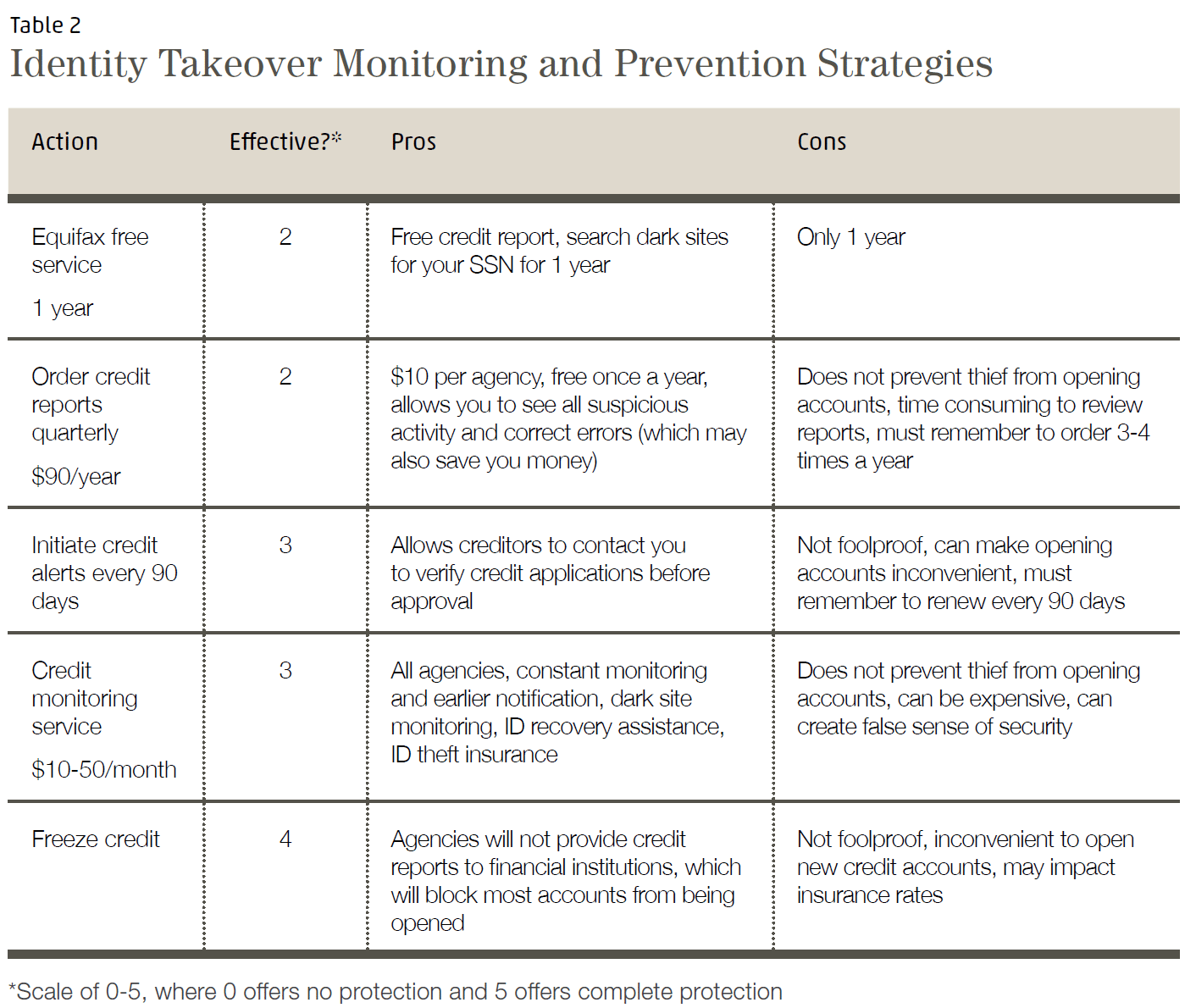
Conclusion
Identity theft continues to increase at an alarming rate, affecting over 6% of consumers in the U.S. last year. MCS recommends that you take measures to increase your cybersecurity and reduce the risk that your identity will be stolen, as well as monitor your accounts so that you identify fraudulent transactions and limit your liability. Please feel free to call me if you would like to discuss cybersecurity and identity theft prevention.
Jeff Yamada, CFP®
jeff@mcsfamilywealth.com
800.525.8808Could my Schwab account be affected by the Equifax Data Breach?
It is highly unlikely that your Schwab accounts would be directly affected. In addition, Schwab offers its Security Guarantee which will cover 100% of losses in your Schwab accounts due to unauthorized activity. You can enhance your own security at Schwab in the following ways:
If you have set up online access to your Schwab accounts, you can:- Make sure you have a strong password when logging in to Schwab
- Set up two-factor authentication for your Schwab login with a security token (contact MCS or Schwab for details)
- Set up Voice ID Authentication or verbal passwords to identify yourself when you call in to Schwab
Resources
- Texas at Austin Center for Identity; Predicting and Explaining Identity Risk, Exposure and Cost Using the Ecosystem of Identity Attributes; Zaeem et al; 2016 https://identity.utexas.edu/assets/uploads/publications/Zaeem-2106-Predicting-and-Explaining-Identity-Risk-Exposure-and-Cost-Using-the-Ecosystem-of-Identity-Attributes.pdf
- Wallethub; Identity Theft: What It Is, How It Happens & the Best Protection; Papadimitriou, Odysseus; 11/29/2016; https://wallethub.com/edu/identity-theft/17120/
- AgingCare.com; Protect Yourself: Steps to Take After a Data Breach; Kerskie, Carrie; 05/16/2017; https://www.agingcare.com/articles/protect-yourself-steps-to-take-after-a-data-breach-200198.htm
- Center for Identity Management and Information Protection; Identity Crimes, Prevention Methods; except from Biegelman, Martin T.; Identity Theft Handbook: Detection, Prevention, and Security, Chapter 20; John Wiley & Sons, inc.; 2009; http://www.utica.edu/academic/institutes/cimip/idcrimes/prevention.cfm
- US Federal Trade Commission; Stopping Unsolicited Mail, Phone Calls, and Emai: https://www.consumer.ftc.gov/articles/0262-stopping-unsolicited-mail-phone-calls-and-email
- Identity Theft Resource Center; http://www.idtheftcenter.org/Fact-Sheets/fs-131.html
- Javelin Strategy & Research; Identity Fraud Hits Record High with 15.4 Million U.S. Victims in 2016, Up 16 Percent According to New Javelin Strategy & Research Study; 02/01/2017; https://www.javelinstrategy.com/press-release/identity-fraud-hits-record-high-154-million-us-victims-2016-16-percent-according-new
- Budnitz, Mark E.; The Legal Framework of Mobile Payments; 02/10/2016; http://www.pewtrusts.org/~/media/assets/2016/02/legal_framework_of_mobile_payments_white_paper.pdf
- Charles Schwab & Co., Inc.; Security Guarantee; http://www.schwab.com/public/schwab/nn/legal_compliance/schwabsafe/security_guarantee.html
